2019: The Fundamentals of AWS Cloud Security – Becky Weiss
Three key elements of secure AWS infrastructure IAM, KMS, VPC
IAM to secure your cloud infrastructure
Basically authentication + authorizations that is needed to reach every single service (API calls), must learn making authenticated API calls, policy language, where to find service specific details.
- For humans: IAM users, Federated identities (Enterprise)
- For applications (roles): EC2, Lambdas, Glue crawler, ECS task, Sagemaker notebooks
Authentication is done via Roles: done for you
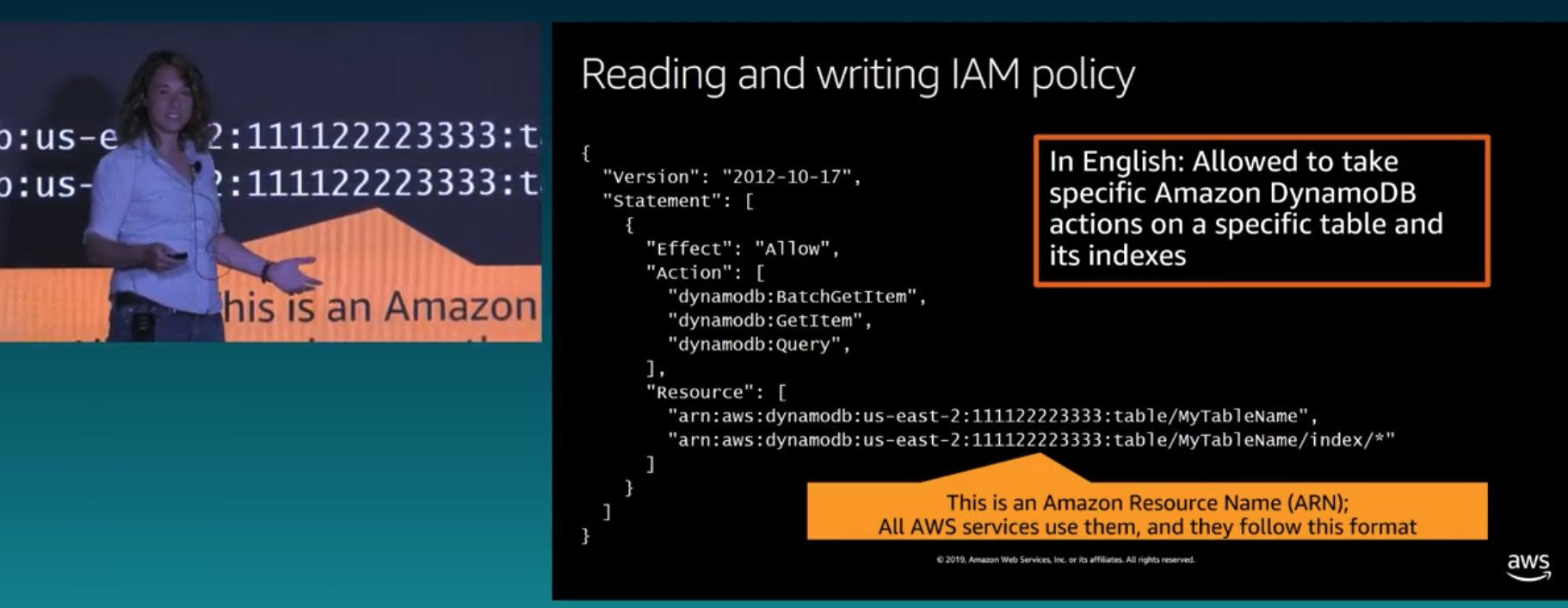
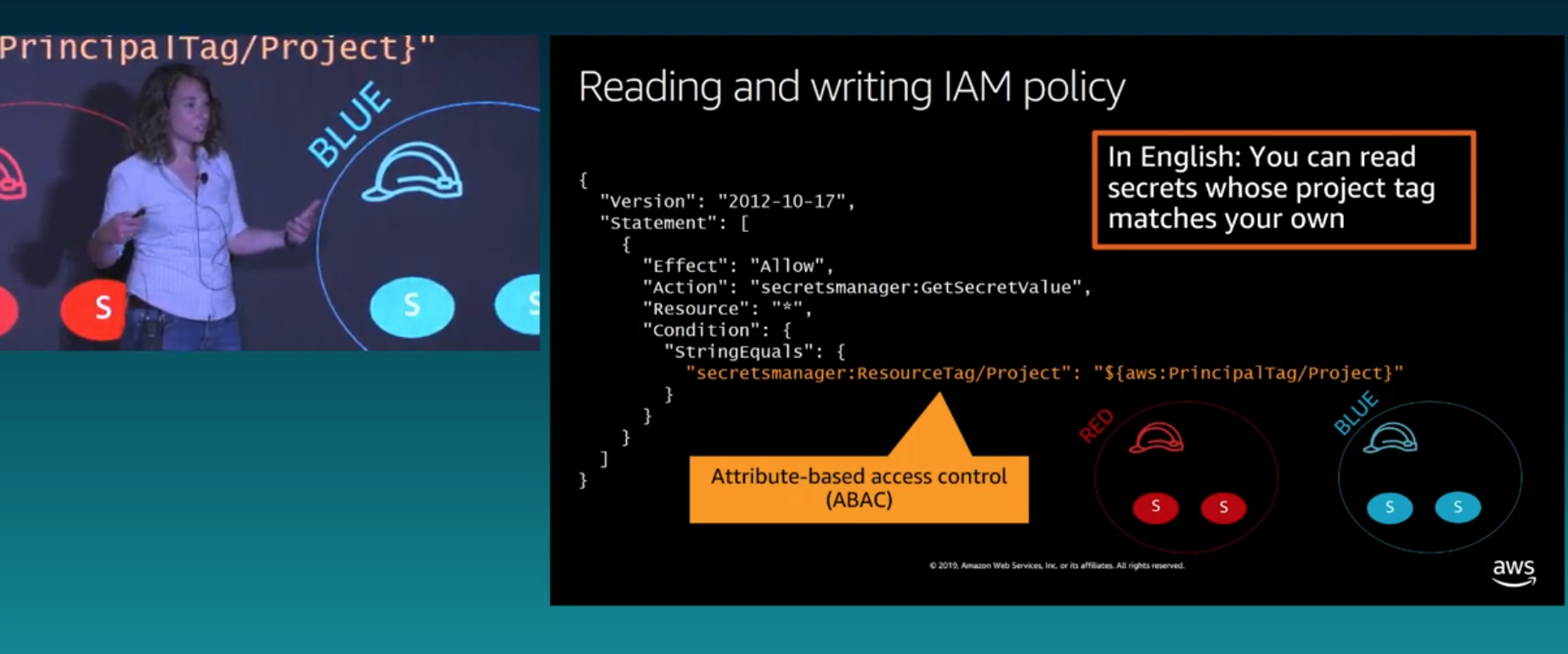
Management console, CLI, Tools & SDKs ⏩ IAM Role ⏩ Signed API request ⏩ ServiceAuthorization is done via Policies: mostly pre-defined but can be tailored to resource level using Amazon Resource Names (ARN), match by attributes like ABAC

To access resources across AWS account boundaries we got options
- Make both sides authorize access: IAM policy (principal request side) + Resource based policy (resource side allowing the principal)
- Attach IAM role to resource then, allow
AsumeRoleon the resource to the principal, then allow Principal role to use theAssumeRoledescribed in the resource (temporary).
AWS Organizations allow you to group multiple accounts and use features like Single Sign-On and organization-, OU-wide service control policies
security invariance: policy that holds true everywhere, e.g, deny a certain region
KMS to secure your data
Managed encrypt and decryption service, in many cases seamlessly integrated and done by default (zero management needed) – Learn how to use, integrations with data-handlers, using control access keys.
- Straightforward to encrypt/decrypt a datum less or equal than 4KB
- Larger encryption is done via envelope encryption, create a transient symmetric data key to encrypt. To decrypt rely on KMS.Decrypt to regenerate a plaintext key to retrieve your data.
- SSE-S3: Server-side encryption AES-256 based, managed by AWS – easiest
- SSE-KMS: A default KMS key by services (e.g., aws/s3) specific for each account is created and can be used immediately OR a CMK (Customer Master Key) can be used for more fine-grained control including specific services.
- IAM Permissions: Caller must haveAllowaccess to both object and key
VPC to secure your network
Virtual data center in the cloud is a network connnecting your infrastructure. It provides the connectivity to/from the infrastructure. Main concepts are subnets, security groups, rouring, private connections.
┌────────────────────────────────────────────────────────────────────────┐
│ Region,e.g.us-east-1 │
│ ┌─────────────────┐ ┌─────────────────┐ ┌─────────────────┐ │
│ │AZ1 │ │AZ2 │ │AZ3 │ │
│ │ ┌──────────────┼─────┼─────────────────┼────┼───────────────┐ │ │
│ │ │VPC │ │ │ │ │ │ │
│ │ │10.0.0.0/ 24 │ │ │ │ │ │ │
│ │ │ │ │ │ │ │ │ │
│ │ │ ┌──────────┐ │ │ ┌─────────────┐ │ │ ┌───────────┐ │ │ │
│ │ │ │Public │ │ │ │Public │ │ │ │Public │ │ │ │
│ │ │ │subnet │ │ │ │subnet │ │ │ │subnet │ │ │ │
│ │ │ └──────────┘ │ │ └─────────────┘ │ │ └───────────┘ │ │ │
│ │ │ │ │ │ │ │ │ │
│ │ │ │ │ │ │ │ │ │
│ │ │ ┌──────────┐ │ │ ┌─────────────┐ │ │ ┌───────────┐ │ │ │
│ │ │ │Private │ │ │ │Private │ │ │ │Private │ │ │ │
│ │ │ │subnet │ │ │ │subnet │ │ │ │subnet │ │ │ │
│ │ │ └──────────┘ │ │ └─────────────┘ │ │ └───────────┘ │ │ │
│ │ │ │ │ │ │ │ │ │
│ │ └──────────────┼─────┼─────────────────┼────┼───────────────┘ │ │
│ │ │ │ │ │ │ │
│ └─────────────────┘ └─────────────────┘ └─────────────────┘ │
│ │
└────────────────────────────────────────────────────────────────────────┘security groups
Configured based on the ingress traffic that you are expecting, e.g., load balancers allow all http traffic. Stateful (what enters the network via connection can leave as well), might refer to other security groups, deny by default.
routing
Some components have access to the internet others not (via IGW). Using route tables to setup these routes.
nat gateways
Usually when a private subnet needs outbound only acess. NAT = Network address translation
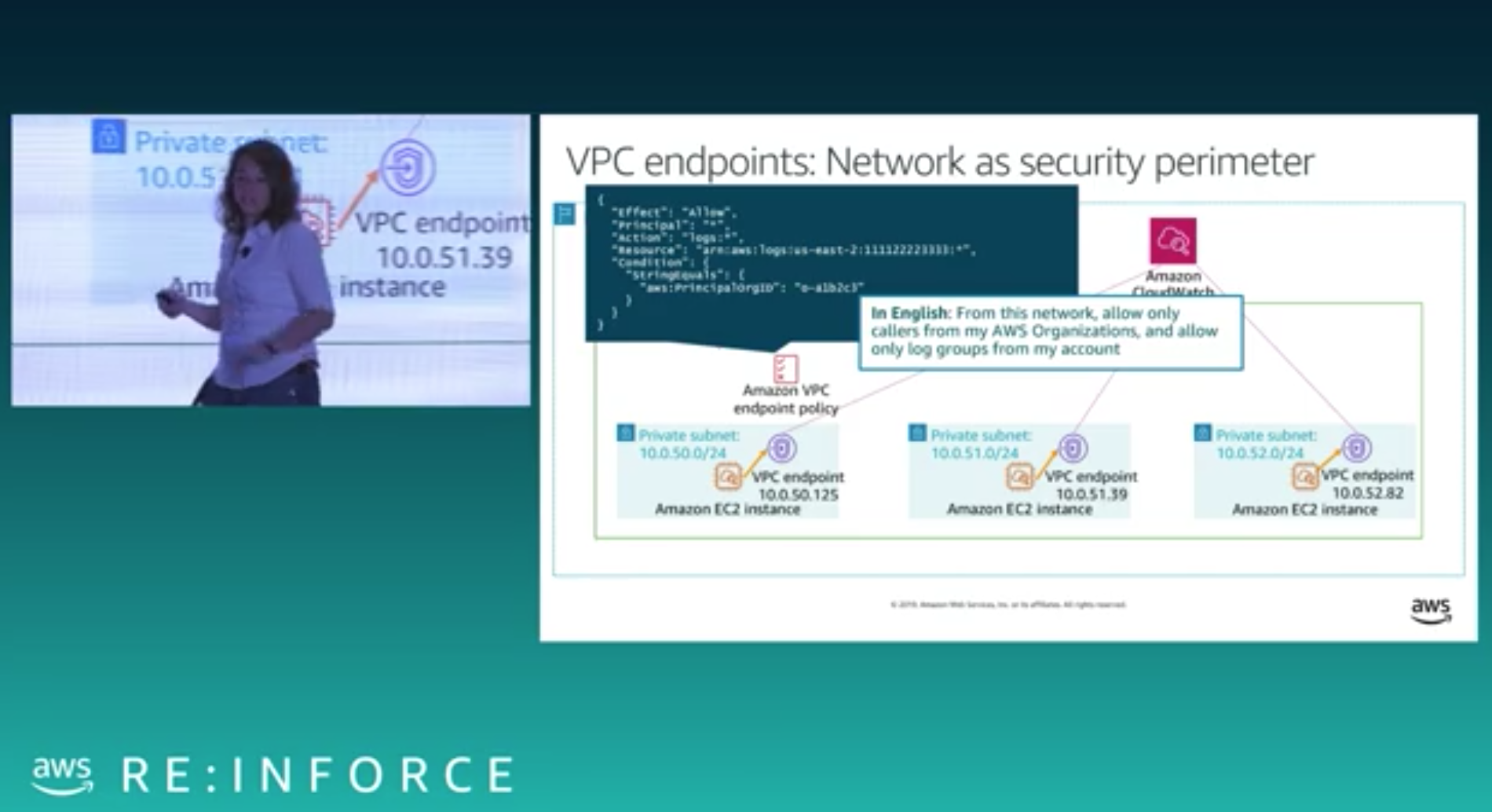
For resources not in your VPC like CloudWatch or S3; VPC endpoints may be used as a security perimeter by limiting access to specific organizations.
2019: Cloud DevSecOps masterclass – Chinmay Tripathi
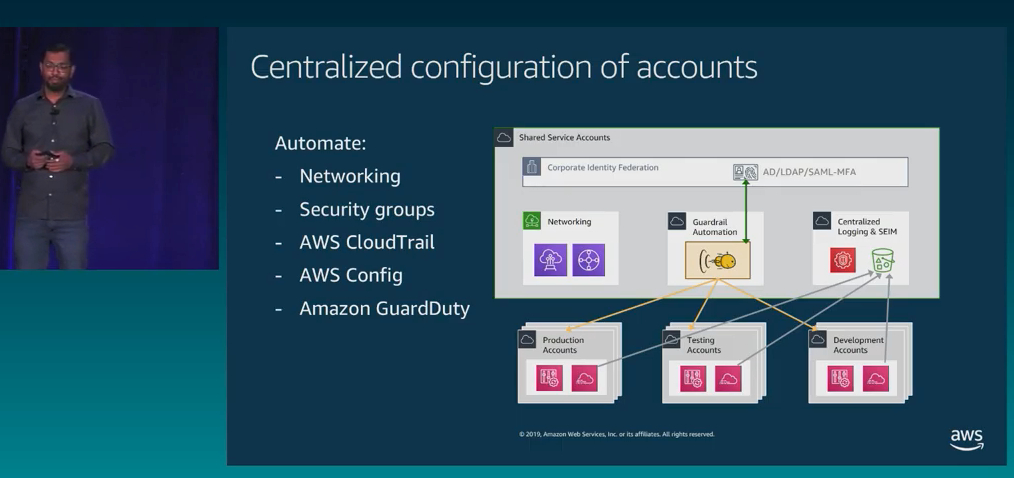
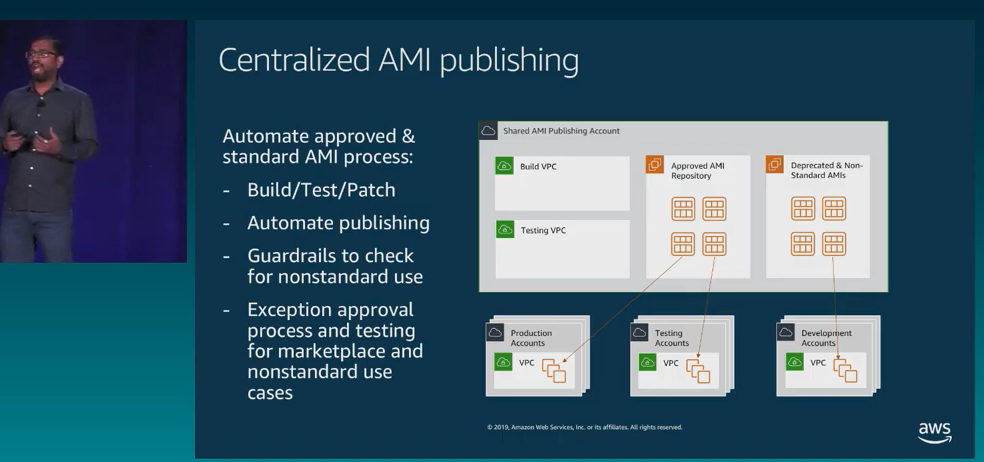
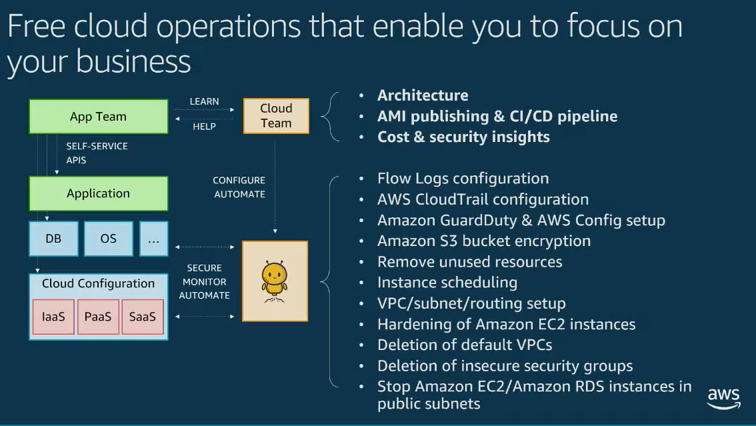
Evolving multi-account architectures
- Innovators: small team, shared goals
- Shared home: several teams sharing accounts and resources
- Hosted service: Centrally managed accounts, still shared by teams
- Multi tenancy: Each project is independent and isolated with set rules